Скачать с ютуб #HITBGSEC в хорошем качестве
Скачать бесплатно и смотреть ютуб-видео без блокировок #HITBGSEC в качестве 4к (2к / 1080p)
У нас вы можете посмотреть бесплатно #HITBGSEC или скачать в максимальном доступном качестве, которое было загружено на ютуб. Для скачивания выберите вариант из формы ниже:
Загрузить музыку / рингтон #HITBGSEC в формате MP3:
Если кнопки скачивания не
загрузились
НАЖМИТЕ ЗДЕСЬ или обновите страницу
Если возникают проблемы со скачиванием, пожалуйста напишите в поддержку по адресу внизу
страницы.
Спасибо за использование сервиса savevideohd.ru
#HITBGSEC
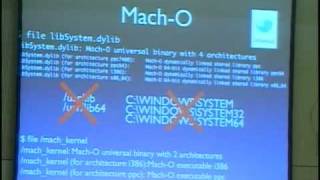
Apple’s Sandboxing (“SeatBelt”) has remained terra incognita since Dionysus Balazakis’s seminal work. 5 years and 300 versions later, however, much as changed. The sandbox has become the linchpin of security in iOS, and the foundation of SIP in OS X 10.11 and later. This talk explores the sandbox in detail, and fills in the gaps from the original work. In particular, we explore the implementations on *OS and OS X, and how they differ. This includes: – Voluntary vs. non-voluntary confinement – Sandbox profiles, both in scheme syntax and binary form – The MACF syscalls hook, primarily ms_sandbox() APIs – Sandboxd (OS X) – ContainerManager (iOS) – Entitlements – Interaction with AMFI All gleaned from reverse engineering, the techniques of which will be of course demonstrated alongside. === CTO of Technologeeks.com, and has been a trainer and consultant in the operating system space for more than 15 years. Author of Mac OS X and iOS Internals (Wiley, 2012), which is slated for release in a 2nd, updated edition soon. Author of “Android Internals: A confectioner’s cookbook” which was released back in October 2014. Taught classes and assisted developers and architects around the world in customizing Android, working around iOS limitations and optimizing performance in mobile environments. Professional clients include Intel, EMC, VMware and others. Taught academically: two semesters of Mobile Architecture Internals for Harvard University.





![[CB16] The ARMs race for kernel protection by Jonathan Levin](https://i.ytimg.com/vi/7qSr5p3wJ_8/mqdefault.jpg)


