Скачать с ютуб RPO, RTO & MTD in Business Continuity & Disaster Recovery | Explained in details with real examples💥 в хорошем качестве
Скачать бесплатно и смотреть ютуб-видео без блокировок RPO, RTO & MTD in Business Continuity & Disaster Recovery | Explained in details with real examples💥 в качестве 4к (2к / 1080p)
У нас вы можете посмотреть бесплатно RPO, RTO & MTD in Business Continuity & Disaster Recovery | Explained in details with real examples💥 или скачать в максимальном доступном качестве, которое было загружено на ютуб. Для скачивания выберите вариант из формы ниже:
Загрузить музыку / рингтон RPO, RTO & MTD in Business Continuity & Disaster Recovery | Explained in details with real examples💥 в формате MP3:
Если кнопки скачивания не
загрузились
НАЖМИТЕ ЗДЕСЬ или обновите страницу
Если возникают проблемы со скачиванием, пожалуйста напишите в поддержку по адресу внизу
страницы.
Спасибо за использование сервиса savevideohd.ru
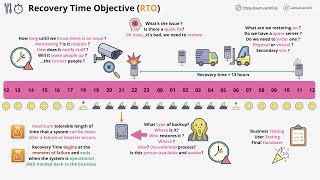
RPO, RTO & MTD in Business Continuity & Disaster Recovery | Explained in details with real examples💥
Bounce Back Faster Than Ever: RPO, RTO & MTD in Business Continuity Explained! Disasters happen, but downtime doesn't have to! This video equips you with the knowledge to ensure a swift recovery. We'll explore RPO (Recovery Point Objective), RTO (Recovery Time Objective), and MTD (Maximum Tolerable Downtime) - the cornerstones of Business Continuity and Disaster Recovery planning. Learn how to define your organization's tolerance for data loss and downtime, and create a plan to get back on track quickly. Become a Business Continuity Master: Understanding the Recovery Trio: Demystify RPO, RTO, and MTD and their roles in disaster preparedness. Data Loss Tolerance: Learn how to define your RPO to minimize data loss after an incident. The Speed of Recovery: Discover how to set realistic RTOs to get your operations back online fast. MTD: The Downtime Threshold: Understand the maximum downtime your business can withstand. Real-World Examples: See these concepts applied to different business scenarios. Building Your Recovery Plan: Gain actionable steps to create a robust Business Continuity plan. Top suggested videos to watch – 1. Change Management: Ultimate Guide for Auditors | Emergency vs Normal Change - • Change Management: Ultimate step by s... 2. Access Control Models: Discretionary vs Mandatory Access Control - • Access Control Models: Why Discretion... 3. Risk Management with Real-life Examples | Risk Assessment on 5X5 matrix - • Risk Management explained with real l... 4. Identification, Authentication, and Authorization in Security - • Understanding Identification, Authent... 5. Risk Appetite vs Risk Tolerance vs Risk Capacity - • Risk Appetite vs Risk Tolerance vs Ri... 6. Demilitarized zone (DMZ) in Network Security - • Demilitarized zone DMZ in Network Sec... 7. CRISC Exam Success Tips: Domains, Strategy, and Resources - • ISACA CRISC Exam Success Tips: Domain... 8. Three lines of Defense model | Risk Governance - • Three lines of Defense model | Risk G... 9. Types of Sensitive information -PII, SPI, and PI - • Types of Sensitive information -PII, ... 10. Encryption & Decryption: Symmetric & Asymmetric - • What is Encryption & Decryption? How ... 11. Security Assessment vs Security Monitoring vs Security Audit - • Security Assessment vs Security Monit... 12. Security Incident vs Security Event vs Security Breach - • Security Incident vs Security Event v... 13. Brute Force Attacks: Prevention Techniques - • Brute Force Attacks: How Hackers Gain... 14. Software Development Life Cycle (SDLC): Overview - • Software Development Life Cycle (SDLC... 15. Different types of hackers - Discussed with examples - • Different types of hackers - White, G... 16. HIPAA - Compliance & Rules - • HIPAA - Compliance & Rules | How to r... 17. OWASP Top 10 Vulnerabilities - • OWASP Top 10 Vulnerabilities. All dis... 18. Vulnerability assessment vs Penetration testing - • Vulnerability assessment vs Penetrati... 19. Test of Design & Test of Effectiveness - • Test of Design & Test of Effectivenes... 20. Types of Audits in Information Security - • Types of Audits in Information Securi... 21. Privacy by Design & Privacy by Default - • Privacy by Design & Privacy by Defaul... 22. Data Security vs Data Privacy - • Data Security vs Data Privacy 🔏 How b... 23. BYOD Policy: Mobile Device Management vs Mobile Application Management - • BYOD Policy - Mobile Device Managemen... 24. Jailbreaking, Rooting & Cracking: Security Risks - • What is Jailbreaking, Rooting & Crack... 25. Information Security vs Cyber Security - / p1tpmxkndv 26. Geofence: Revolutionizing Marketing - • What is Geofence? How does it work? H... 27. Overview of network protocols - • Overview of different network protoco... 28. Digital Signatures vs Electronic Signature - • Why Digital Signatures are more secur... 29. Importance of Clock Synchronization in ISMS 27001 - • Why Clock Synchronisation is required... 30. Information & Data Classification Policy - • Information & Data Classification Pol... 31. RPO, RTO & MTD in Business Continuity & Disaster Recovery - • RPO, RTO & MTD in Business Continuity... 32. Inherent Risk and Residual Risk - • What is Inherent Risk and Residual Ri... 33. KRI vs KPI vs KCI - • KRI vs KPI vs KCI 💥 Relationship b/w ... 34. Leading vs Lagging Indicators - • Leading vs Lagging Indicators 💥 How t... 35. Intellectual Property - Trademark, Copyright, Patents & Trade Secret - • Intellectual Property - Trademark, Co... #RPO #RTO #MTD #BusinessContinuity #DisasterRecovery #BusinessPreparedness #Downtime #DataRecovery #IncidentResponse #BusinessPlanning #RiskManagement #CyberSecurity #Compliance #BusinessContinuityPlan #BCP #DRP #ITSecurity #DataProtection #BusinessAnalysis #RiskAssessment #BusinessTips #growthikigai #BusinessResilience #ITInfrastructure #DataSecurity #DataBackup #EmergencyResponse #BusinessStrategy #RiskMitigation #SecurityPlanning #CyberThreats #RegulatoryCompliance #RiskAwareness #StrategicPlanning #OperationalResilience #InformationSecurity #RiskAvoidance #CyberDefense #BusinessDevelopment #StrategicManagement #CyberAwareness #DataPrivacy #businessgrowth #RiskPlanning #RiskResponse #RiskStrategy #RiskMonitoring #RiskIdentification #RiskReporting #RiskCulture #RiskFramework #BusinessStrategy #RiskSolutions #RiskEducation #RiskLeadership #RiskConsulting #RiskAdvisory #RiskInsights