Скачать с ютуб What are certificates? в хорошем качестве
Скачать бесплатно и смотреть ютуб-видео без блокировок What are certificates? в качестве 4к (2к / 1080p)
У нас вы можете посмотреть бесплатно What are certificates? или скачать в максимальном доступном качестве, которое было загружено на ютуб. Для скачивания выберите вариант из формы ниже:
Загрузить музыку / рингтон What are certificates? в формате MP3:
Если кнопки скачивания не
загрузились
НАЖМИТЕ ЗДЕСЬ или обновите страницу
Если возникают проблемы со скачиванием, пожалуйста напишите в поддержку по адресу внизу
страницы.
Спасибо за использование сервиса savevideohd.ru
What are certificates?
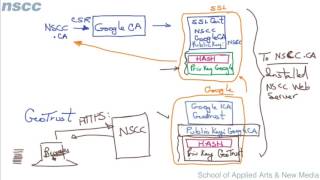
Certificates are used to prove identity and used for creating secure communication. Check out http://itfreetraining.com for more of our always free training videos. This video looks at how a certificate works, what is a certificate and how they are used for identification and secure communication. Download the PDF handout http://itfreetraining.com/handouts/ce... What is a certificate? A certificate is an electronic document that contains data fields. When compared to a traditional paper certificate there are some similarities between an electronic certificate and a physical certificate. Digital certificates like a physical certificate are issued by an authority. For example, a university may issue a certificate to a student to show that they have completed the necessary work in order to graduate. The next question is, would you trust a physically certificate? Digital certificates work the same way. They are issued from an authority and the question becomes would you trust the authority that issued the certificate? Electronic certificates also contain other fields like who or what the certificate was issued to, how long it is valid, the public key and the digital signature. If a digital certificate is presented to a user or computer, the user or computer is able to check the certificate to ensure the person using it should be using it. Also the certificate contains a digital signature which allows the certificate to be checked to make sure it has not been modified. Digital Signature A digital signature provides a method for a certificate to be checked to ensure it has not been modified. In order to do this, a hash value is created for the certificate. To generate a hash value the certificate is put through a function to create a single value. Hash functions are designed so different certificates will not produce the same value, however the hash value cannot be used to generate the original certificate. The same principal applies to a person's fingerprints. They can be used to identify a person, however using a finger print you could not work out the features of a person like what color hair they have. When a certificate is created, the hash value for that certificate is also created. Using a function involving the private key, a digital signature is created and added to the certificate. Digital Signature Example When a certificate is used, in order to check the certificate has not been changed, the following is done: The computer generates the hash value for the certificate. Next, the digital signature is put through a function using the public key which should result in the same hash value. If both values match, the certificate has not been modified. This prevents a 3rd party taking a certificate, changing the values in the certificate and using the certificate. Trust Model Certificates work off a trust model. An example of a trust model in computers is that a computer may have a sticker on it indicating which operating systems it will run. The consumer, seeing this sticker, must trust that the manufacture would not put this sticker on the laptop unless it will run that operating system. The customer must also trust the creator of that operating system would not allow a computer manufacturer to put a sticker on a computer that would not run that operating system. Certificate Trust Model Certificates are generally deployed in a hierarchy. At the top is the root certificate authority. This can be an internal Certificate Authority or an external authority like VeriSign. When an authority like VeriSign issues a certificate, they will perform a number of checks on the individual purchasing the certificate to ensure that they are a valid business. When a certificate is used it can be checked to see which authority issued that certificate. In order for the certificate to be used, the computer must trust the authority that it was issued from. Authorities like VeriSign are trusted by default on most operating systems. Certificate Error If a certificate is presented to the computer and it is not trusted, the computer will generate an error asking if the users want to trust the certificate. It is up to the user to decide if they believe the certificate is valid. Certificate Hierarchy Certificates use a hierarchy. At the top is the root CA, below these are subordinate CA's. Any level can issue certificates to subordinate CA's or direct to users, computers or devices. If the user, computer or device trusts the root CA, then any certificate that is issued by any CA in the hierarchy will automatically be trusted and thus used by the client. References "MCTS 70-640 Configuring Windows Server 2008 Active Directory Second edition" pg 771-775 "Public key certificate" http://en.wikipedia.org/wiki/Public_k...